Directory Services
Directory Services section allows you to configure integration with Azure Active Directory.
Microsoft Configuration
Register the application in Azure Active Directory as described in the Microsoft documentation: https://learn.microsoft.com/en-us/power-apps/developer/data-platform/walkthrough-register-app-azure-active-directory
Requirements for setting up application registration:
- Supported account types should be set as: "Accounts in any organizational directory (Any Azure AD directory - Multitenant)"
- Application platform must be set as Web
- Redirect URI must be set to https://YOUR_PBX_FQDN/service/oauth2/microsoft/callback (replace YOUR_PBX_FQDN with your real FQDN)
- Implicit grant flows and hybrid flows should be set as: "Access tokens (used for implicit flows)" and "ID tokens (used for implicit and hybrid flows)"
A new Client secret should be created in the "Certificates & secrets" menu (note and save the value of the Client secret in notepad as this value will only be shown once)
Please make sure that you save the Client ID and Client Secret once they are provided by Microsoft - you will need them when configuring Azure Active Directory integration in Thirdlane.
The following delegated permissions must be granted (followed by the "Grant admin consent" action) from the API permissions menu:
- offline_access
- User.Read
- User.Read.all
- Directory.Read.all
Required fields in user accounts for synchronizing Azure Active Directory users with PBX:
- First name
- Last name
- Work phone. This field will be used as an extension number for User Extensions in Thirdlane PBX
Note that there is a delay between information changes in Azure Active Directory and those changes being available for synchronization.
Thirdlane Configuration
Once you completed configuration on Microsoft side, you can use this screen to configure Azure AD for the tenant.
Click the Create Directory Service Integration button to create a Directory Service integration.
Create Directory Service Integration
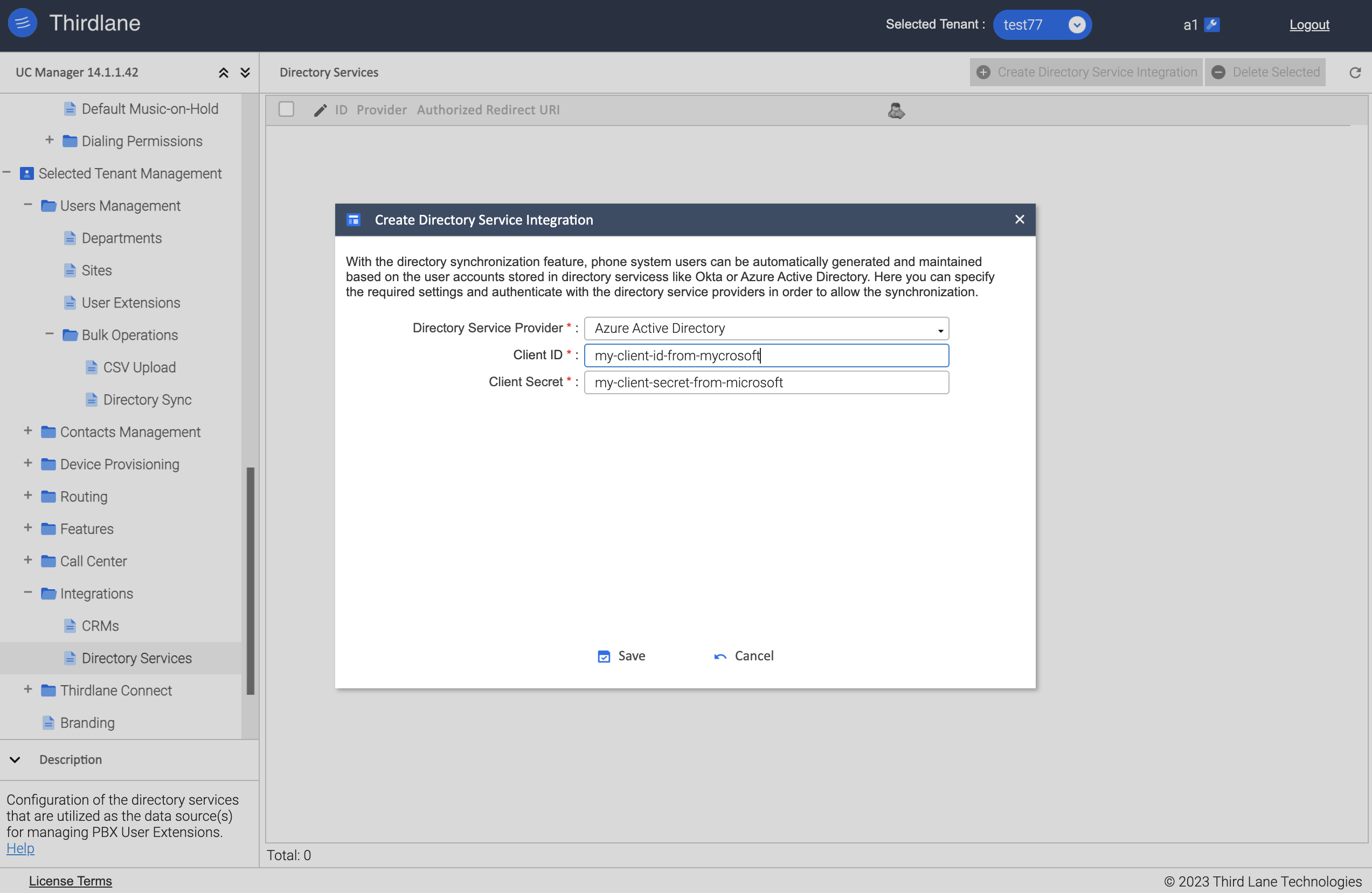
Directory Service Provider. Select Directory Service Provider (currently Azure Active Directory is the only option).
Client ID. Enter Client ID obtained from Microsoft.
Client Secret. Enter Client Secret obtained from Microsoft.
Authentication
Once the data is saved, you have to authenticate as a user who will have read access to Azure AD.
Click on the icon with the image of a "person" to start authentication. When the authentication is completed, refresh the screen. A green indicator should appear if the authentication was successful.
Note that after configuring Azure AD integration and authenticating, you will have to perform the first manual Directory Sync.