Security
Security section is used for management of SIP protocol security options such as Banned SIP User Agents, Traffic Spike Control and Other Options.
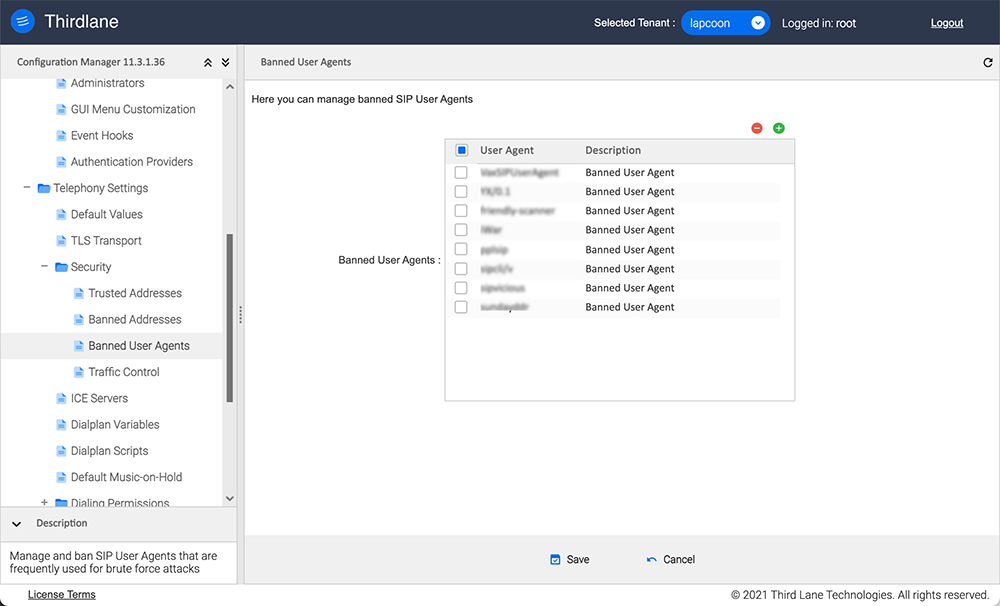
Banned User Agents
This section allows you to ban SIP User Agents that are frequently used for brute force attacks.
Enable Banning User Agents. Enables User Agent verification against the list. This is enabled by default.
Banned User Agents. This list is pre-populated by default with User Agents known to be used for SIP system hacking.
Traffic Spike Control
In this section you can configure maximum rate of incoming SIP traffic and what to do when these limits are exceeded.
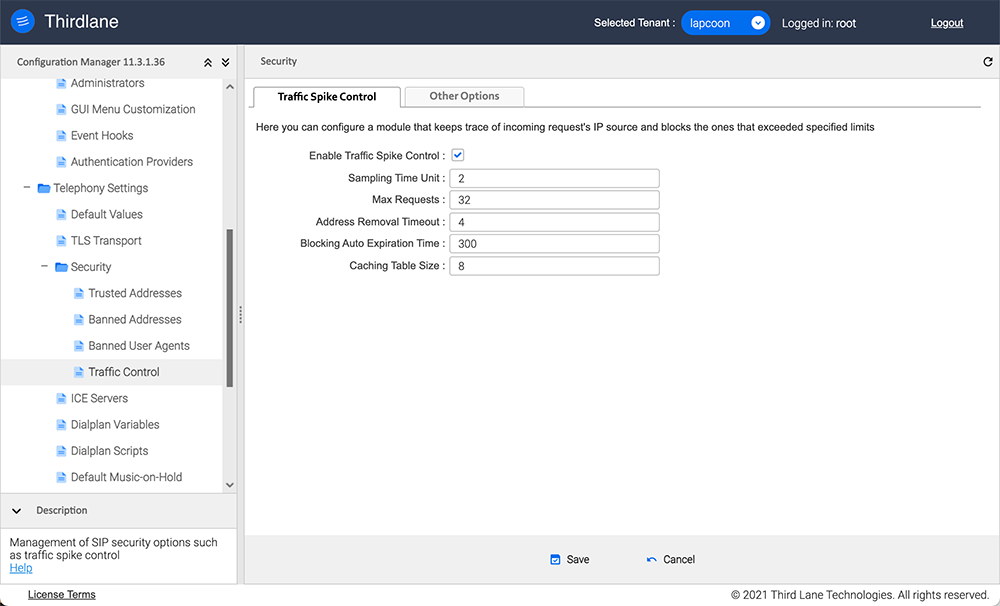
Enable Traffic Spike Control. Enables limiting incoming requests and blocks source IP address that exceeds it. It is enabled by default.
Sampling Time Unit. Time period in seconds used for sampling. A too small value may lead to performance penalties.
Max Requests. How many requests should be allowed per Sampling Time Unit before blocking all the incoming requests from source IP address.
Address Removal Timeout. Specify for how long the IP address will be kept in memory after the last request from that IP address in order to count subsequent requests.
Blocking Auto Expiration Time. Time period in seconds used to keep source IP address in the banned IPs list.
Max Number of Addresses. Number specifying the size of ban hash table. The possible range is from 2 to 31.
It is strongly recommended to set Max Requests to a small number and make Address Removal Timeout as long as possible, while using Source IP Whitelist to process all SIP traffic from known addresses without possibility of blocking it.
Other Options
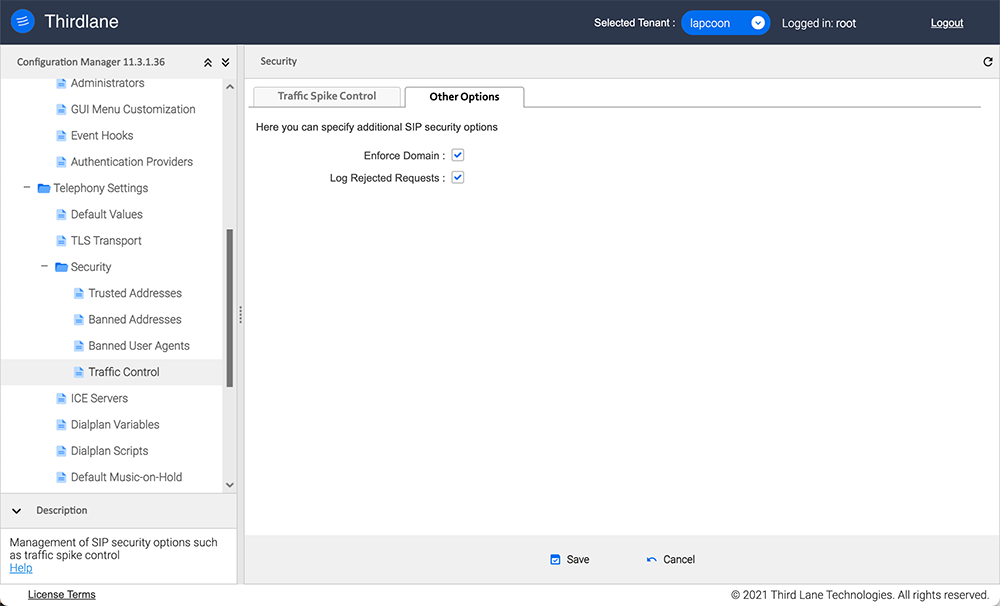
Enforce Domain. Allow registrations only from domains specified in the Domains and SSL section.
Log Rejected Requests. Write all the rejected SIP requests to /var/log/rejected_requests.log. Use this option with caution and do not leave it enabled as this may generate a large file.